In einer Welt, in der Nachhaltigkeit mehr als nur ein Trend ist, sondern eine Notwendigkeit, haben Innovationen im Bereich der erneuerbaren Energien eine zentrale Bedeutung erlangt. Eine dieser bahnbrechenden Innovationen ist die effiziente Nutzung von Solarwechselrichtern, die nicht nur umweltfreundlich, sondern auch wirtschaftlich vorteilhaft sind. Durch die Integration smarter Technologien in unseren Alltag haben wir jetzt die einzigartige Möglichkeit, unsere Energiegewohnheiten in Echtzeit zu überwachen und zu optimieren. Stell dir vor, du könntest mit einer App genau sehen, wie viel Strom du gerade produzierst und verbrauchst – klingt praktisch, oder?
 Record radio stations usig NixOS and systemd-timers Featured Image
Record radio stations usig NixOS and systemd-timers Featured Image
 Record radio stations usig NixOS and systemd-timers Featured Image
Record radio stations usig NixOS and systemd-timers Featured Image
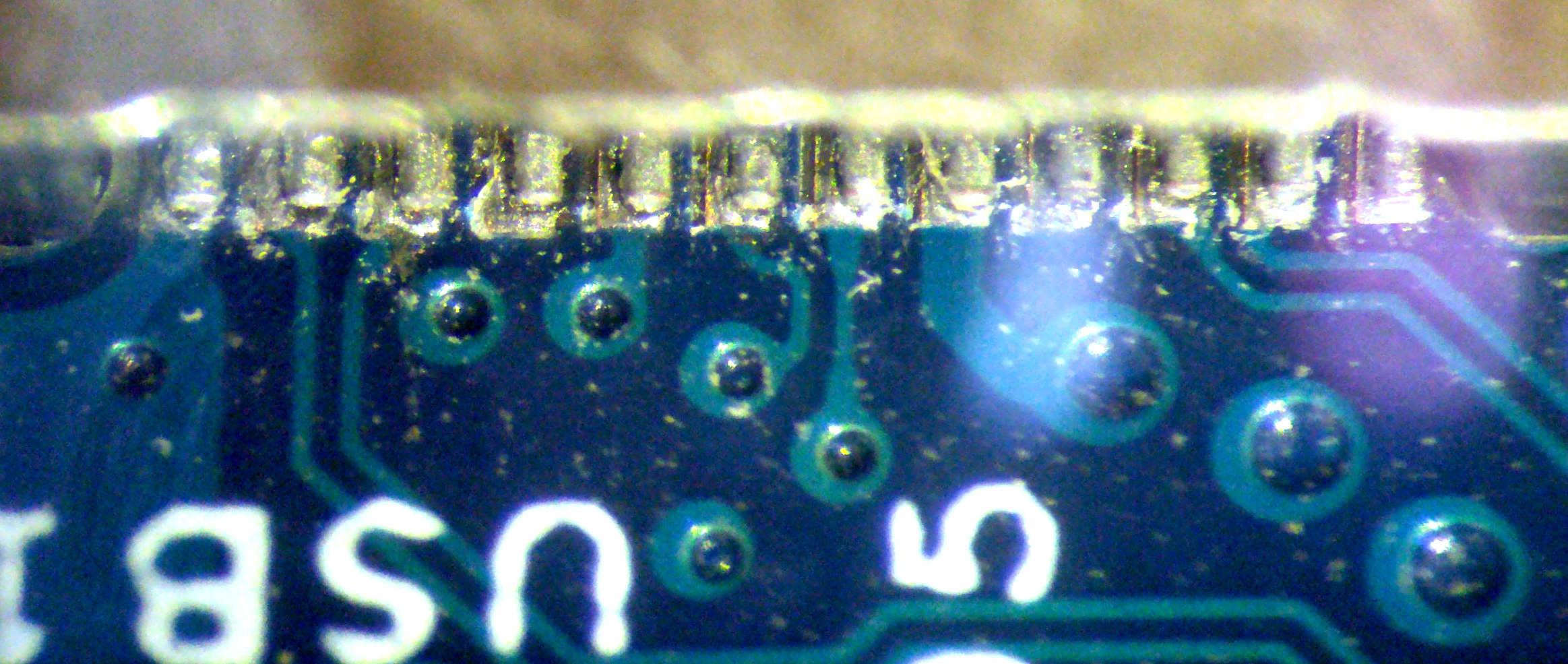 Fix unchargeable Thinkpad L390 by cold solder joints of USB-C-Sockets Featured Image
Fix unchargeable Thinkpad L390 by cold solder joints of USB-C-Sockets Featured Image
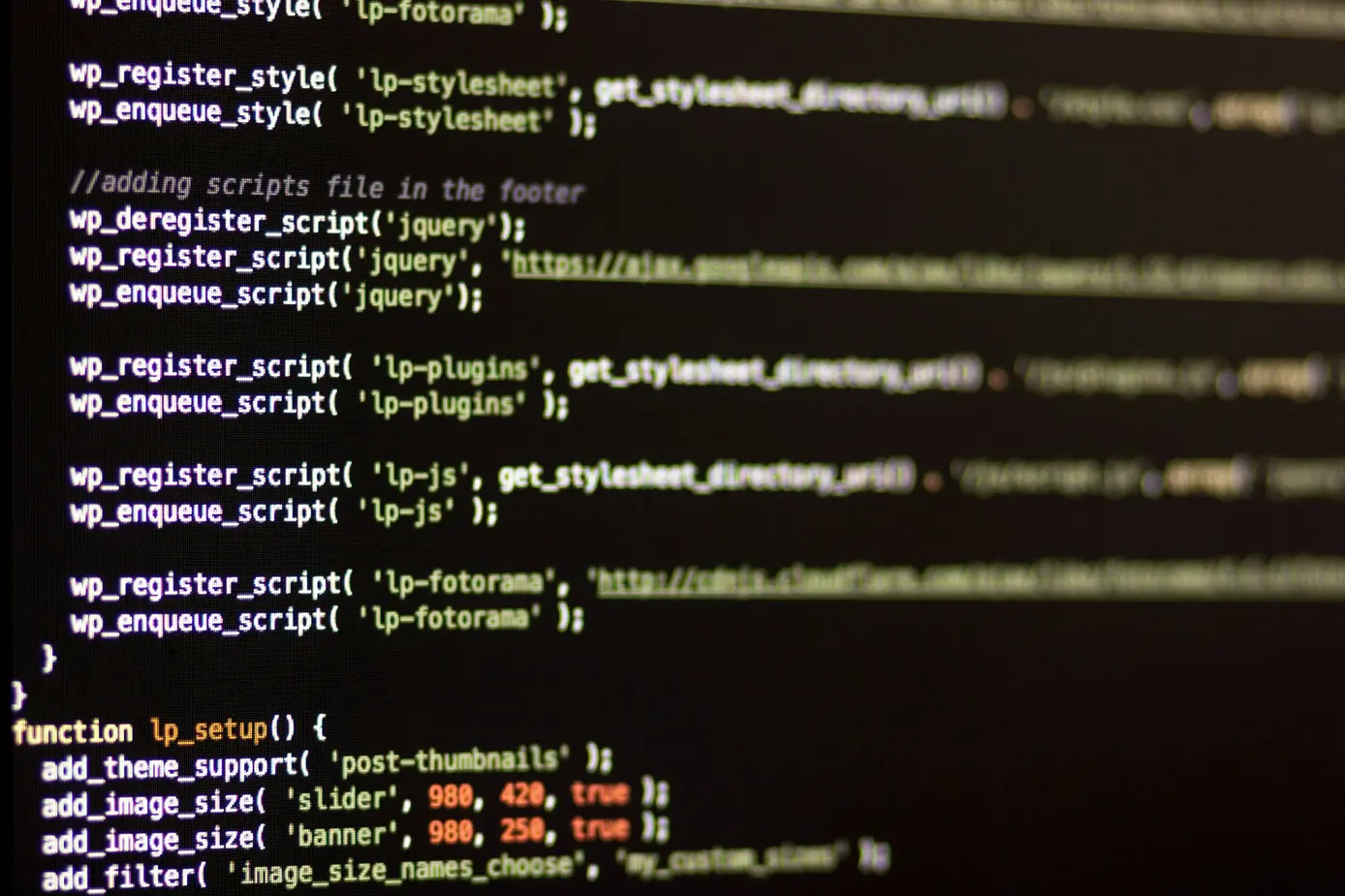 Nix Flake development environment for WordPress Featured Image
Nix Flake development environment for WordPress Featured Image
 Innovative Nutzung von Solarwechselrichtern Featured Image
Innovative Nutzung von Solarwechselrichtern Featured Image
 Linux WSL2 printing server on Windows 10 Featured Image
Linux WSL2 printing server on Windows 10 Featured Image
 Drawing Faces 360 – like you mean it! Tutorial and Technical Breakdown Featured Image
Drawing Faces 360 – like you mean it! Tutorial and Technical Breakdown Featured Image
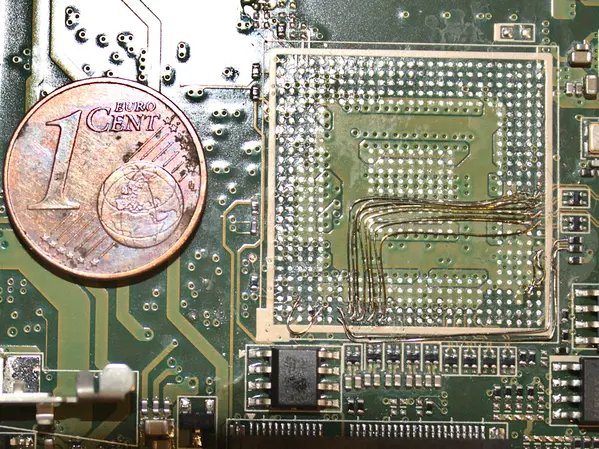 Replacing defective BGA-Chip with wires on Wacom Cintiq Companion 2 tablet Featured Image
Replacing defective BGA-Chip with wires on Wacom Cintiq Companion 2 tablet Featured Image
 Nextcloud development environment on NixOS Featured Image
Nextcloud development environment on NixOS Featured Image
